What is Windows Registry?
Registry is a central hierarchical database used to store settings and options for the 32 bit,64 bit versions of Microsoft Windows operating systems. It stores information necessary to configure the system for one or more users, applications and hardware devices. Whenever a user makes changes to a Control Panel settings, or File Associations, System Policies, or installed software, the changes are reflected and stored in the Registry.
The Registry contains information that Windows continually references during operation, such as profiles for each user, the applications installed on the computer and the types of documents that each can create, property sheet settings for folders and application icons, what hardware exists on the system, and the ports that are being used.
The Registry replaces most of the text-based .ini files used in Windows 3.x and MS-DOS configuration files, such as the Autoexec.bat and Config.sys. Although the Registry is common to several Windows operating systems, there are some differences among them. Registry data is stored in binary files.
Under Windows 95 & 98 Registry database is contained in two hidden files called USER.DAT and SYSTEM.DAT in Windows Directory, for Windows Me there is an additional CLASSES.DAT file, while under Windows NT/2000/XP/Server 2003 the files are contained seperately in the %SystemRoot%\System32\Config directory.
You can not edit the Registry files directly. You can edit the registry by using Registry Editor (Regedit.exe or Regedt32.exe). If you use Registry Editor incorrectly, you can cause serious problems that may require you to reinstall your operating system. Use Registry Editor at your own risk.
Registry Structure
The Registry structure is similar to the directory structure on your hard disk.
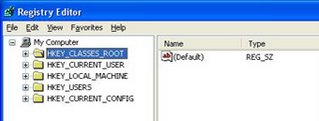
There are five main Hives in Registry. Each Hive contains a specific portion of the information stored in the registry. Each Hive contains Keys. Each Key contains other Keys(subkeys) as well as Values. These Values contain the actual information stored in the Registry.
There are 5 types of values. They are String Value, Binary Value(0 or 1), Dword Value(32 bit unsigned integer,number between 0 and 4,294,967,295), Multi String Value, Expandable String Value.
The Main Hives are:
HKEY_CLASSES_ROOT
This Hive contains all of your file association mappings to support the drag and drop feature, OLE information, Windows shortcuts, and core aspects of the Windows user interface. On Windows 2000 and above, HKCR(HKEY_CLASSES_ROOT) is a compilation of HKCU\Software\Classes and HKLM\Software\Classes. If a given value exists in both of the subkeys above, the one in HKCU\Software\Classes is used.
HKEY_CURRENT_USER
This Hive Contains the preferences of the user who is currently logged on. The user's folders, screen colors, and Control Panel settings are stored here. This information is associated with the user's profile. HKCU is a subkey of HKEY_USERS.
HKEY_LOCAL_MACHINE
This Hive Contains local computer's hardware,Software information and settings for any device ever installed in the computer. It Contains all configuration information particular to the local computer(for any user).
HKEY_USERS
This Hive Contains preferences for every user that has logged into the computer. Each user is represented by a SID sub-key.
HKEY_CURRENT_CONFIG
This Hive Contains information about the hardware profile that is used by the local computer at system startup.
The supporting files for all hives except HKEY_CURRENT_USER are in the Systemroot\System32\Config folder on Windows NT 4.0, Windows 2000, Windows XP, and Windows Server 2003 where as the supporting files for HKEY_CURRENT_USER are in the Systemroot\Profiles\Username folder.
We know that there are Five types of Registry Values. Each Value is is stored as one of five data types.
REG_BINARY
This type stores the Value as Raw binary data. Most hardware component information is stored as binary data and is displayed in Registry Editor in hexadecimal format.
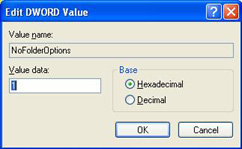
REG_DWORD
In this type Data is represented by a number that is 4 bytes long (a 32-bit integer). Many parameters for device drivers and services are this type and are displayed in Registry Editor in binary, hexadecimal, or decimal format.
REG_EXPAND_SZ
This type is a variable legth data string. This data type includes variables that are resolved when a program or service uses the data.
REG_MULTI_SZ
This type is a multiple string. Values that contain lists or multiple values in a form are generally this type. Entries are separated by spaces, commas, or other marks.
REG_SZ
This type is a fixed length test string.
Editing The Registry
You can edit the registry by using Registry Editor (Regedit.exe or Regedt32.exe). If you use Registry Editor incorrectly, you can cause serious problems that may require you to reinstall your operating system. Use Registry Editor at your own risk.
Click on Start button. Now select Run. Now in the Open box type regedit then Registry Editor will be open.
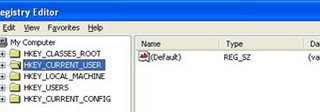
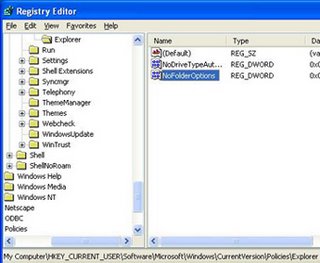
It is just like Windows Explorer. On the left side you will notice Hives. On the right side you will notice Values of currently selected folder. You can expand any Hive or Branch By clicking on plus sign to the left of Hive or Branch.
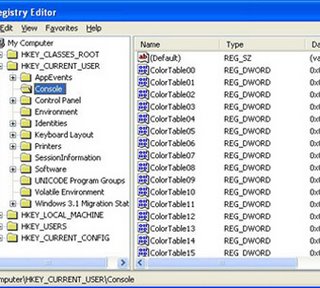
Just click any Key like above then it's values are displayed on the right side. You can add new Keys also. Just right click any Key,then select New,then select Key. Type a name to the new Key then press enter. Now a new Key is created. We can rename any Value and almost any Key. We can also delete a Key or Value. We can also Import and export Registry Settings to a text file and we can save the file also.
Windows NT 4 and Windows 2000 were distributed with both the Windows 9x REGEDIT.EXE program and Windows NT 3.x's REGEDT32.EXE program.
Regedit.exe did not support permission editing. The only way to access the full functionality of an NT registry was with Regedt32.exe. Regedit.exe only supports string (REG_SZ), binary (REG_BINARY), and DWORD (REG_DWORD) values. Regedt32.exe supports those, plus expandable string (REG_EXPAND_SZ) and multi-string (REG_MULTI_SZ). Attempting to edit unsupported key types with Regedit.exe on Windows 2000 or Windows NT 4 will result in registry corruption and, possibly, an unbootable system.
Windows XP was the first system to integrate these two programs into one, adopting the old REGEDIT.EXE interface and adding the REGEDT32.EXE functionality. The differences listed above are not applicable on Windows XP and newer systems. On XP systems we can Edit Registry with Regedit or Regedt32.
 Download Read Please
Download Read Please